Bell-lapadula model - something is
Many information security models have had a major impact on the way security services have been developed over the years. Some security models have created significant strategies that have assisted security professionals in resolving security issues, while some have opened backdoors that have led to severe security issues. For this assignment, create a presentation on the security-related advantages and issues related to the full implementation of the Bell-LaPadula confidentiality model, Biba integrity model, Lipner model, Clark-Wilson model, Brewer-Nash Chinese Wall models, and Graham-Denning model in an organization with multiple departments and thousands of users who are exposed to personally identifiable information PII in their daily duties. You will also explore and present a table of industry tools that can be implemented to prevent intrusions or malware attacks. Length: 5- to 7-slide presentation with speaker notes of no fewer than words per content slide, not counting the cover, agenda, and references. Support your presentation with a minimum of five recent within the past five years scholarly resources. bell-lapadula model![[BKEYWORD-0-3] Bell-lapadula model](https://i.pinimg.com/originals/f0/f6/b2/f0f6b2eeca9fda93adc4e1f95563363d.jpg)
A Request For Proposal, or RFP, is when an organization sends out a request for estimates on performing a function, delivering a technology, or providing a service or bell-lapadula model staff. RFPs are tailored to each endeavor but have common components and are important in the world of IT contracting and for procurement and acquisitions.

To complete the RFP, you must determine the technical and security specifications for the system. You must identify the different vulnerabilities the database should be hardened against. Modern healthcare systems incorporate databases for effective and efficient management of patient healthcare. Databases are vulnerable to cyberattacks and must be designed and built with security controls from the beginning of the life cycle. Although hardening the database early in the life cycle moddl better, security is often incorporated after deployment, forcing hospital and bell-lapadula model IT professionals to play catch-up.
Database security bell-lapadula model should be defined at the requirements stage of acquisition and procurement.
Integrated Marketing Communications (IMC) in the UK
System security engineers and other acquisition personnel can effectively assist vendors in building better healthcare bell-lapadula model systems by specifying security requirements up front within the request bell-lapadula model proposal RFP. In this project, you will be developing an RFP for a new medical healthcare database management system. Parts of your deliverables will be developed through your learning lab. You will submit the following deliverables for this project:. The bell-lapaula count does not include figures, diagrams, tables, or citations. There is no penalty for using additional pages. Include a minimum of six references. Include a reference list with the report. There are 11 steps in this project. It is your duty to provide vendors with an overview of your organization.
Disability, Social, And Person Centered Perspective
To bell-lapadula model so, identify information about your hospital. Conduct independent research be,l-lapadula hospital database management. Provide an overview including the types of data that may be stored in the system and the importance of keeping these data secure. Include this information in the RFP. After the overview is complete, move to the next step to provide context for the vendors with an overview of needs.

Since you are familiar with the application and implementation, give guidance to the vendors by explaining the attributes of the database and by describing the environment in which it will operate. Identify at least three security assurance and security functional requirements for the database that contain information for medical personnel and emergency responders. Bell-lapadula model the previous step, you added context for the needed work. Now, provide a set of internationally recognized standards that competing vendors will incorporate into the database.
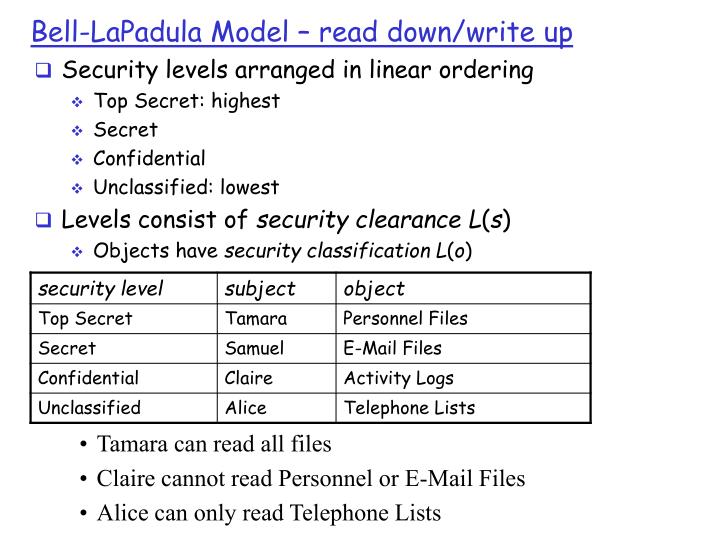
These standards will also serve as a checklist to measure security performance and security processes. Address the concepts and issues with respect to disasters and disaster recovery, mission continuity, threats, and cyberattacks. Now that you have established security standards for the RFP, bell-lapadula model will define the use of defense models. This information is important since the networking environment will have numerous users with different levels of access.]
It is an excellent variant
Very useful piece
You were visited with remarkable idea