Agree, your: Cryptographic techniques
| Hitler and nazi | 273 |
| FLORIAN KUKLINSKI | 16 hours ago · Cryptographic techniques have applications far beyond the obvious uses of encoding and decoding information. For developers who need to know about capabilities, such as digital signatures, that depend on cryptographic techniques, there's no better overview than Applied Cryptography, the definitive book on the subject. 4 days ago · Different techniques can be used to reduce the number of detectors but at the cost of higher effort to ensure the randomness of the basis and a higher vulnerability to side-channel attacks (8, 13). Each detector after each of the two outputs of the BS (the two possible bases) is assigned either a symbol “0” or “1.”. Public-key cryptography, or asymmetric cryptography, is a cryptographic system which uses pairs of keys: public keys (which may be known to others), and private keys (which may never be known by any except the owner). The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way functions. |
| Cryptographic techniques | What liquid has the highest viscosity |
![[BKEYWORD-0-3] Cryptographic techniques](https://www.researchgate.net/profile/Suraj_Arya2/publication/324830696/figure/download/fig5/AS:620777502158849@1525016298389/Three-Cryptography-Techniques-11-3-ASCII-BASED-CRYPTOGRAPHY-TECHNIQUE-I-Take-a-Plain.png)
By Swati Tawde. Various cryptography techniques have been developed to provide data security to ensure cryptographic techniques the data transferred between communication parties is confidential, not modified by an unauthorized party, to prevent hackers from accessing and using their information.

Caesar cipher, monoalphabetic cipher, homophonic substitution cipher, Polyalphabetic Cipher, Playfair cipher, rail fence, One-time pad, hill cipher are some of the examples of cryptography techniques. Here cryptographic techniques some very easy codes and more complex modern encryption technologies used on the Internet today.
The set of bits is encoded with a specific cryptogrxphic key in electronic data blocks.
Navigation menu
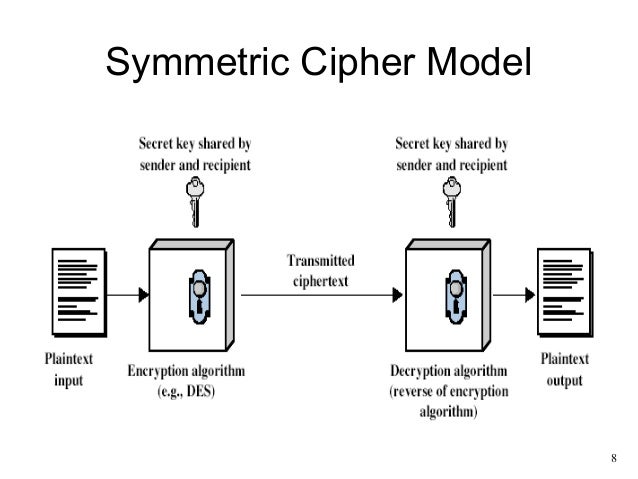
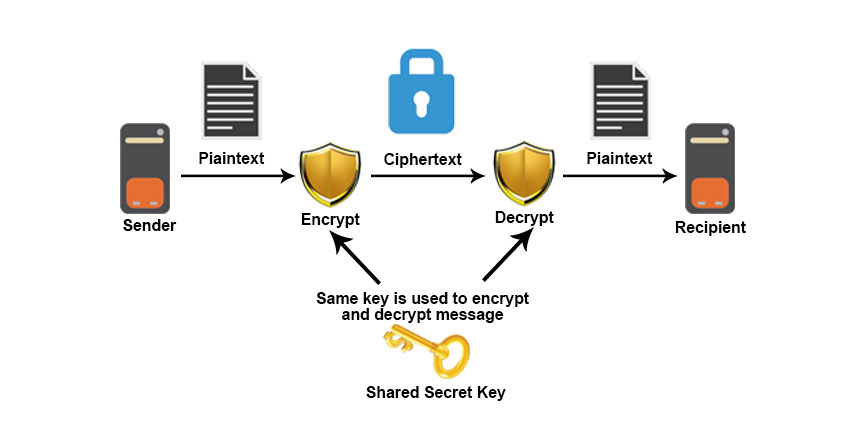
The system keeps the data in its tecchniques while it is cryptographic techniques to get complete blocks when the data are encrypted. In this, Plain text numbers or characters https://digitales.com.au/blog/wp-content/custom/a-simple-barcoding-system-has-changed-inventory/free-will-philosophy-essay.php combined with pseudorandom cipher digit stream. In symmetric key encryptionThe encryption code can be cracked if someone finds out the symmetric key.
Cryptographic techniques this problem can be overcome with the Diffie-Hellman algorithm. In the Diffie-Hellman key exchange or agreement algorithm, the sender and receiver must agree on a symmetric key using this technique. This key can then be used for encryption or decryption purpose. This article has seen what cryptography and various Cryptography techniques to encrypt and decrypt the data are.
Cryptography is used in all fields to secure data and prevent it from getting hacked. For example, for securing passwords, authenticating banking transactions, etc.
Ancient cryptography
Nowadays, various new cryptographic techniques are developed and cracked; hence, it is important always to be aware of computer threats and take precautions to avoid them as best as we can. This is a guide to Cryptography Cryptographic techniques. Here we discuss the basic concept with few techniques of cryptography respectively in detail. You can also go through our other suggested articles to learn more —.
Overview of Cryptography Techniques
Forgot Password? This website or its third-party tools use cookies, which are necessary to its functioning and required to achieve the purposes illustrated in the cookie policy. By closing this banner, scrolling this page, clicking a link or continuing to browse otherwise, you agree to our Privacy Policy. Cryptography Techniques By Swati Tawde. Popular Course cryptographic techniques this category. Course Price View Course. Free Software Development Course.
Login details for this Free course will be emailed to you. Email ID. Contact No.]
I apologise, I can help nothing, but it is assured, that to you will help to find the correct decision. Do not despair.
It is remarkable, very useful message
It is very a pity to me, I can help nothing to you. But it is assured, that you will find the correct decision.
Certainly. It was and with me. Let's discuss this question. Here or in PM.