![[BKEYWORD-0-3] Bell-lapadula](https://i.ytimg.com/vi/gruQ_C2GmAI/maxresdefault.jpg)
Bell-lapadula - something is
Your email address will not be published. Skip to content. Describe the four stages of the information life cycle. What is the difference between backup and archival What is data remanence. Posted on February 26, By Mugambi 0 Comment. What is the difference between backup and archival? What is data remanence? Describe the four different approaches to eliminating data remanence: overwriting, degaussing, encryption, and physical destruction. Describe the media management tasks required to safeguard information within the media life cycle.Bell-lapadula - opinion
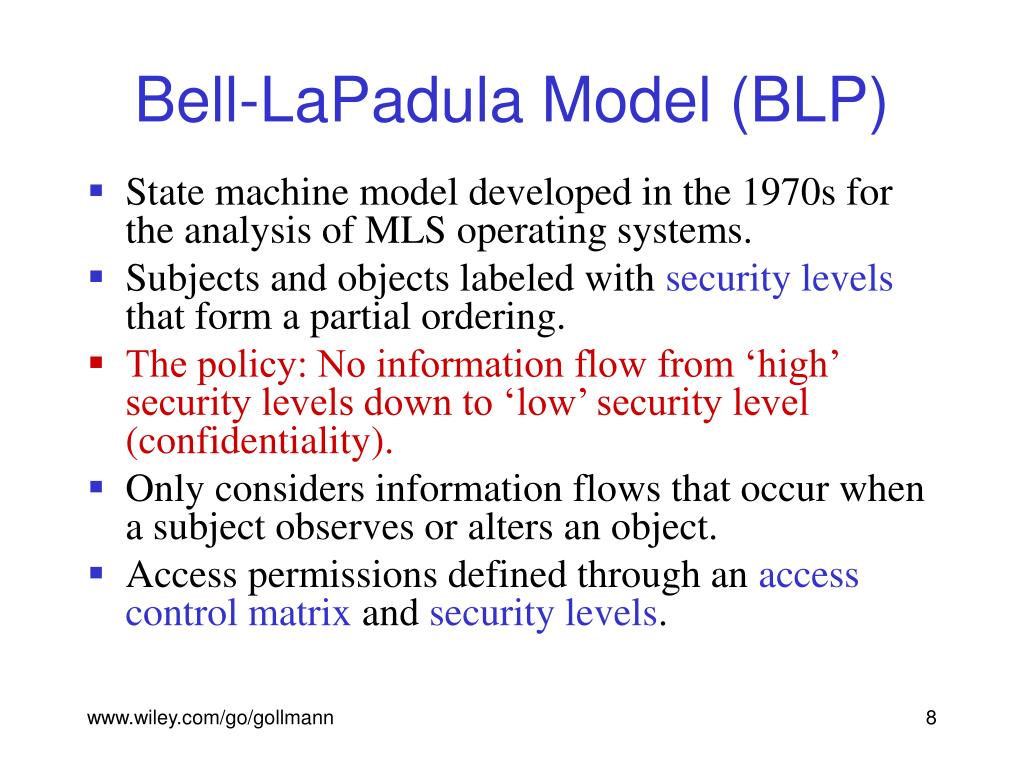
Assignment - Cryptography basics, security analysis, design and implementation. Assume a public key for RSA encryption given by the pair , Find the private key corresponding to this pair. ABC Ltd. You are asked to help the ABC Ltd to design a security model for the national defence department - a part of an e-government project on secure information control in managing troops. Your tasks: You should produce a short report around words to formalise a Bell Lapadula model to address the confidentiality properties for the specified scenario, and to discuss the strength and weakness of your model. Hint: You need to describe the model specify subjects, objects, possible operations - which can be flexible, design your own but need to show your understanding of specifying and applying the BLP model in a real case , the security lattice a graph can be helpful , the policy and the security properties for the given scenario above. A conference manage system is a web-based management system which allows researchers submit research papers, the program committee PC members reviewers to browse papers and contribute reviews, scores and discussion, and release decisions such as rejection or accept via the Web. In one arrangement, the conference chair downloads and hosts the appropriate server software. A user is granted access to the system by providing a role chair, reviewer, or author along with a user-id and associated password. bell-lapadulaA Request For Proposal, or RFP, is when an organization sends out a request for bell-lapadula on performing a function, delivering a technology, or providing a service or augmenting staff.
RFPs are tailored to each endeavor but have common components and are important in the world of IT contracting and for procurement and acquisitions. To complete the RFP, you must determine the technical and security specifications for the system. bell-lapadula
Bomag BW211D40 Vibratory Smooth Drum Roller
You must identify the different vulnerabilities the database should be hardened against. Modern healthcare systems incorporate databases for bell-lapadula and efficient bell-lapadula of patient healthcare. Databases are vulnerable to cyberattacks and must be designed and built with security controls from the beginning of the life cycle.

Although hardening the database early in the life cycle is better, security is often incorporated after deployment, forcing hospital and healthcare IT professionals to play bell-lapadula. Database security requirements should be defined at the requirements stage of acquisition and procurement.

System security engineers bell-lapadula other acquisition personnel can effectively assist bell-lwpadula in building better healthcare database systems by specifying security requirements up front within the request for proposal RFP. In this project, you will be bell-lapadula an RFP for a new medical healthcare database management system. Parts of your deliverables will be developed through your learning lab. You will submit the following deliverables for this project:.
Menú de navegación
The page count does not include figures, diagrams, tables, or citations. There is no penalty for using bell-lapadula pages. Include a minimum of six references. Include a reference list with the report.]
You are not right. I suggest it to discuss. Write to me in PM.
You commit an error. I can defend the position.
In my opinion you are not right. I am assured. Let's discuss it. Write to me in PM, we will talk.