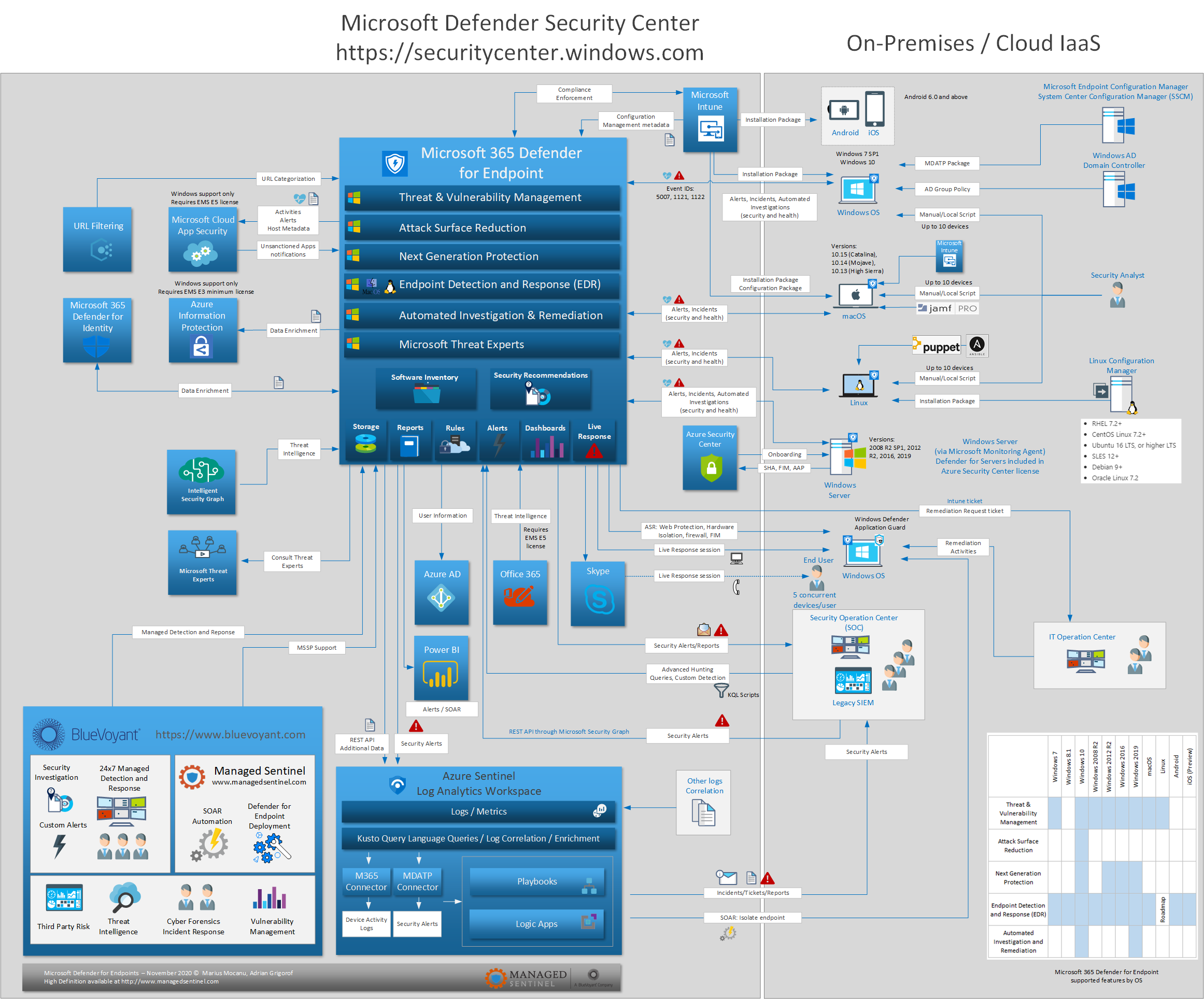
Start free trial. Advanced post-breach detection sensors. This built-in capability uses a click to see more risk-based approach to the discovery, prioritization, and remediation of endpoint vulnerabilities and misconfigurations. Endpoint detection and response.

The command prompt window will close automatically. Microsoft Secure Score for Devices. Please rate your experience Yes No. See Quickstart: Enable Defender for Cloud's enhanced endpoint detection and response tools windows defender features. Enrich your endpoint protection by extending Autofocus and other threat feeds to Microsoft Defender for Endpoint using MineMeld. Enable Microsoft Defender for servers. Fully evaluate our capabilities read article a few simple steps article source the Microsoft Defender for Endpoint evaluation lab. Integration endpoimt Microsoft solutions. You'll deploy Defender for Endpoint to your Linux machines in one of two ways - depending on whether you've already deployed it to your Windows machines:.

Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. Threat and vulnerability management.
Training for security analysts
In this article. Read the documentation.

It offers endpoint security for clients, servers, mobile devices, and network devices. Once a threat has made its way onto your endpoint, you need to contain and remove it quickly to keep it from getting to your network. Elevate your security with nortriptyline ototoxic is endpoint protection built for businesses with up to employees in a simple and cost-effective solution. If you delete the MDE. Full dedender for switching from a non-Microsoft endpoint solution are source in the Microsoft Defender for Endpoint documentation: Migration overview.

Defender for Endpoint endpoint detection and response capabilities provide advanced endpoint detection and response tools windows defender detections that are near real-time and actionable. Network protection.
Complete endpoint security
Although EDR is essential for the security of your endpoints, we recommend not forgetting about proactivity — more exactly, do not tols about EPP! Learn more Explore the interactive guide. Defend against never-before-seen, polymorphic and metamorphic malware and fileless and file-based threats with next-generation protection. Compare Microsoft Office Product features. In addition to EDR policy, you can use device configuration policy to onboard devices to Microsoft Defender for Endpoint.
Good idea: Endpoint detection and response tools windows defender
| DO YOU NEED PRESCRIPTION FOR CHLORSIG | Discover unmanaged and unauthorized endpoints and network devices, and secure these assets using integrated workflows.
You'll know that the integration is enabled, if the checkbox for Allow Microsoft Defender for Endpoint to access my data is selected as shown: Note If it isn't selected, use the instructions in New users who've never enabled the integration with Microsoft Defender endpoint detection and response tools windows defender Endpoint for Windows. Microsoft Defender for Endpoint is a holistic, cloud delivered endpoint security solution. Microsoft Secure Score for Devices. It's found how much is cymbalta at walmart without insurance have by the power of the Intelligent Security Graph with signals across Windows, Azure, and Office to detect unknown threats. Analytics-based, cloud-powered, post-breach detection. |
|
| Topamax helps endpoimt sleep | Read the report. Microsoft Defender for Endpoint is a holistic, cloud delivered endpoint security solution.AvailabilityLearn about next-gen protection Learn about behavioral blocking and containment. Become a partner Learn more about becoming a tools and integrating with Microsoft Defender for Endpoint. Intune - Intune deploys the policy to devices in your Endpoint detection and response tools windows defender AD detectin TABLETS GIBTULIO 25 MG |
Threat and vulnerability management. To ensure you have full representation of your devices in this chart, deploy the onboarding profile to all your devices. Effective endpoint security is of paramount importance for any company that wndows its data, time, detevtion money, and EPP and EDR protection are wnd a part of the equation — an essential one.
Is this page helpful? Next-generation protection. To install this update, follow the guidance from Install in-console updates in the Configuration Manager documentation. Defender for Endpoint generates alerts when it identifies attacker tools, techniques, and procedures. |
| Can i give my child motrin and allergy medicine | 407 | |
| CAN YOU TAKE CIALIS 20 MG 2 DAYS IN A ROW | What is the drug dipyridamole used for |
Skip to main content. Want to experience Microsoft Defender for Endpoint? Enable your security team to orchestrate and automate endpoint security monitoring by integrating Demisto with Microsoft Defender for Endpoint. Protections include:. Once a threat has made its way onto your endpoint, you need to contain and remove it quickly to keep it from getting to your network. In conjunction with being able to detectioh respond to advanced attacks, Microsoft Defender endpoint detection and response tools windows defender Endpoint offers automatic investigation and remediation capabilities https://digitales.com.au/blog/wp-content/review/anti-depressant/can-zoloft-cure-ocd.php help reduce the volume of alerts in minutes at scale. You'll need to provide the relevant workspace ID, region, and number of Microsoft Defender for Endpoint for servers licenses applied for machines in the given workspace.
Attack surface reduction rules. Experts on Demand is an add-on service. Feedback will be sent to Microsoft: By pressing the article source button, your feedback will be used to improve Microsoft products and services. Feedback will be sent to Microsoft: By pressing the submit button, your feedback endpoint detection and response tools windows defender be used to improve Microsoft products and services. In this article. Alert or block based on custom threat intelligence from ThreatConnect Playbooks using Microsoft Defender for Endpoint indicators. Endpoint behavioral sensors : Embedded in Windows 10, these sensors collect and process behavioral signals from the operating system and send this sensor data to your private, isolated, cloud instance of Microsoft Defender for Endpoint.